moectf
xtea
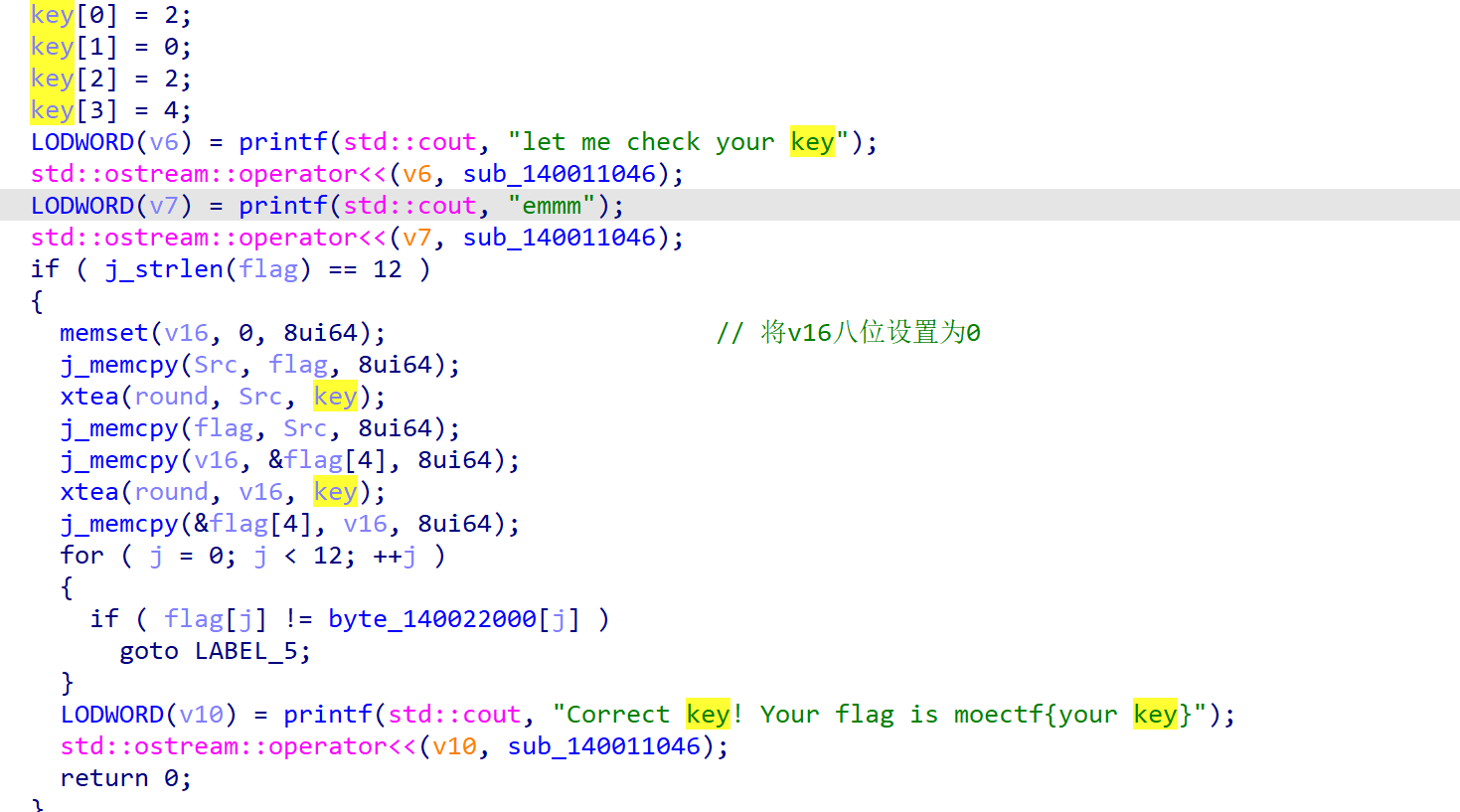
1 | 通过分析我们看出这是两个tea加密,只要两次tea即可解出 |
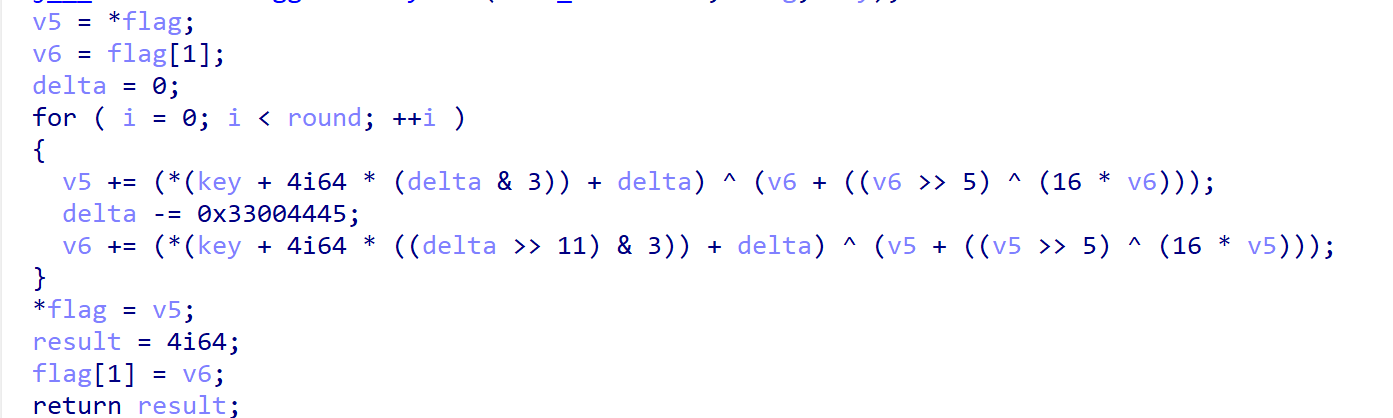
1 | 看tea里面,这个逆向很简单 |
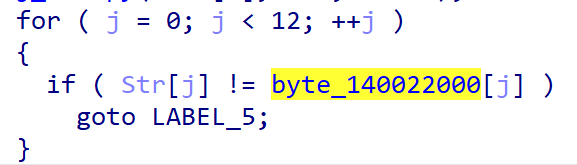
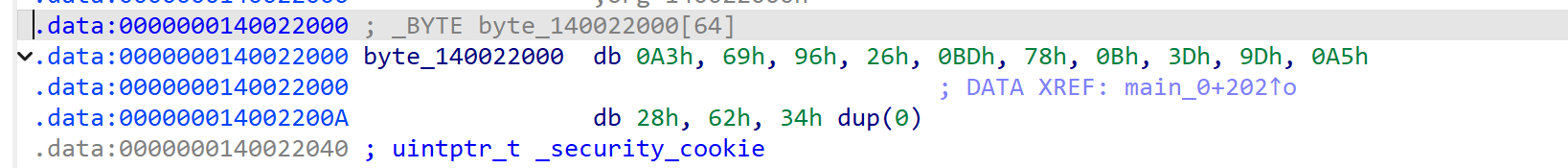
1 | 通过判断语句,找到加密后的flag,注意是小端序存储,也就是0x269669a3 3d0b78bd 6228a59d |
1 | 之后就是反过来解密,先是flag的后八位解密,然后flag更新,把更新后flag的前八位解密,最后十六进制转字符串 |
1 |
|
xxtea
1 | #include <stdio.h> |
moejvav
先用jadx打开
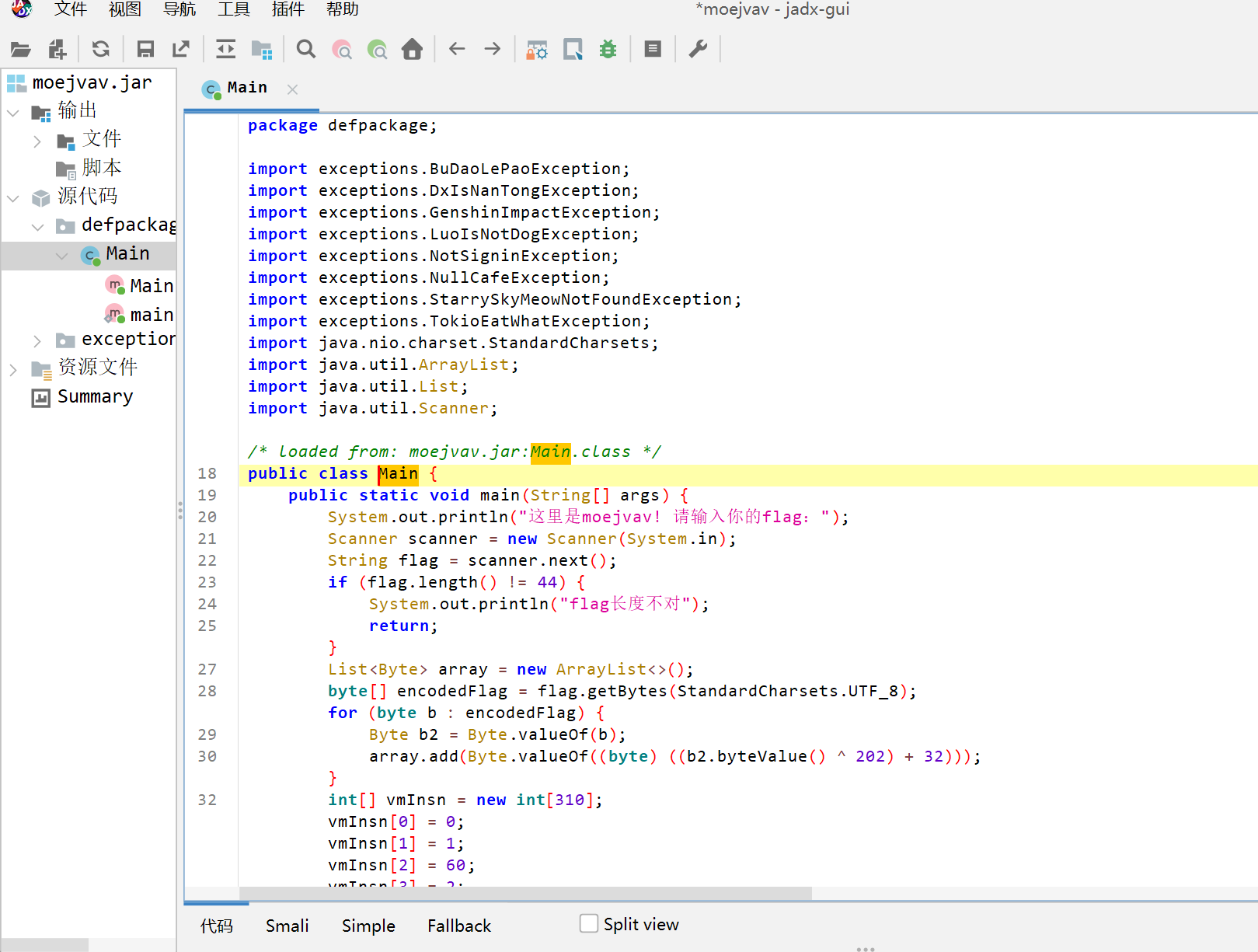
分析代码
1 | 先是把(flag^202)+32 |
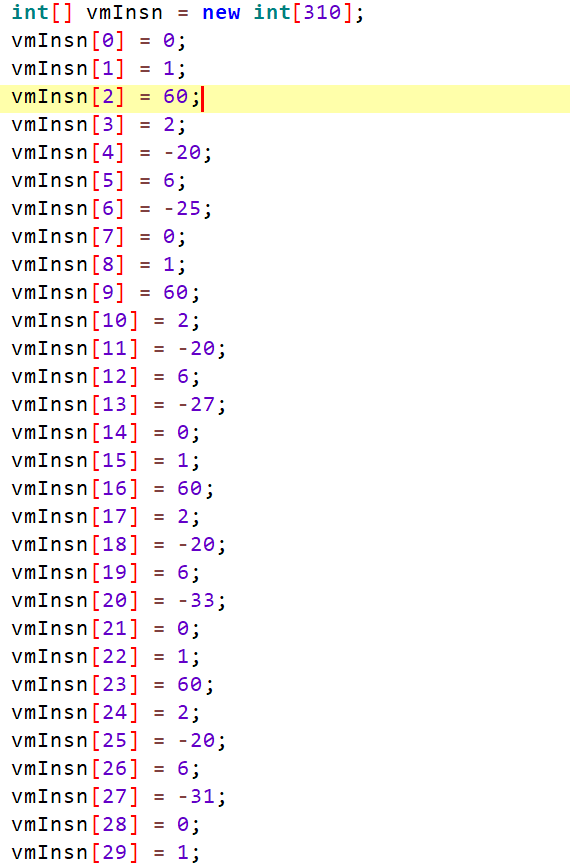
1 | 一个vminsn数组,先不管他 |
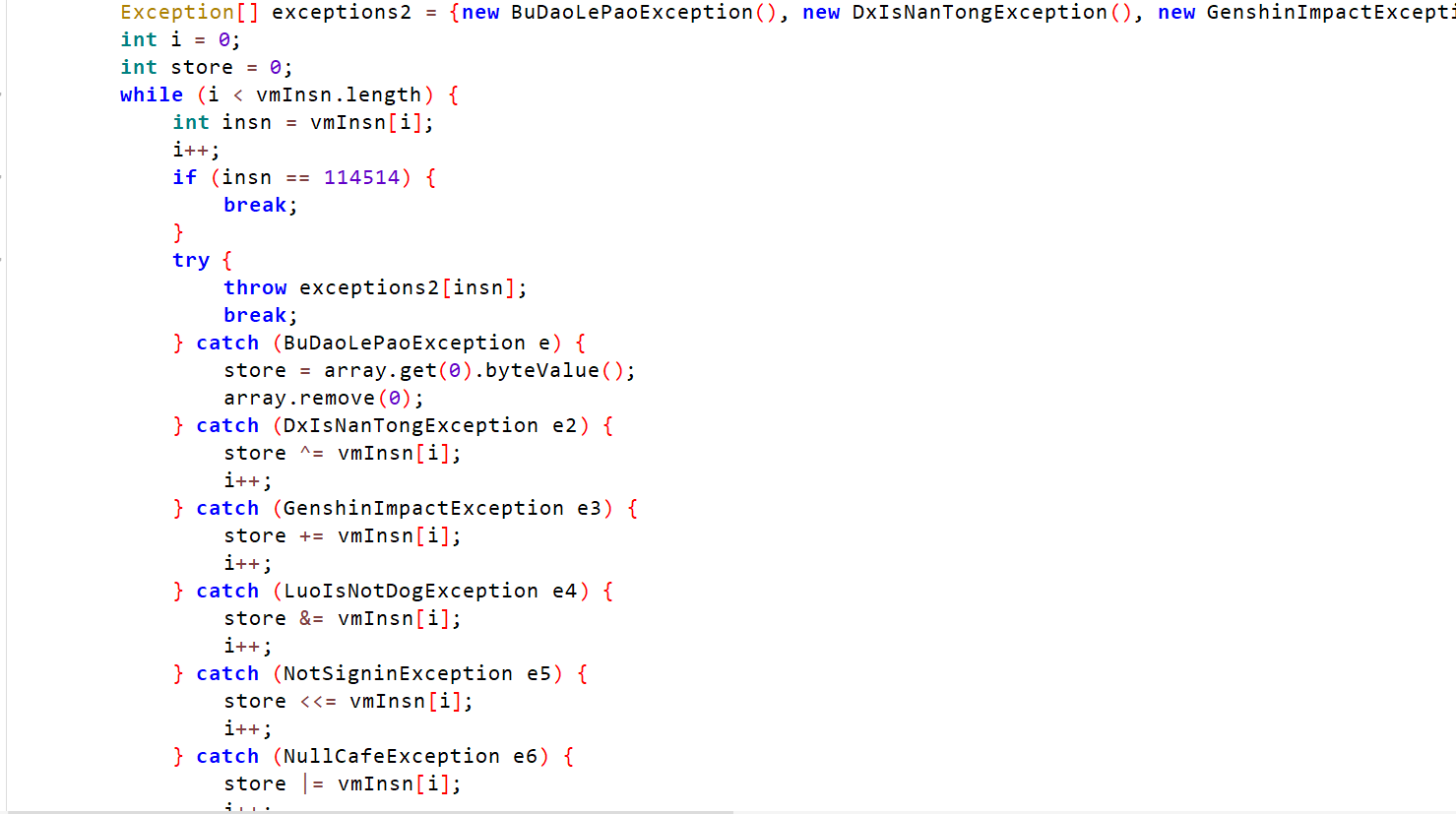
1 | 关键信息: |
1 | 再联系数组分析: |
最终代码:
1 | vmInsn = [0] * 310 |
moedaily
参考博客:MoeCTF2024-wp_moectf2024官方wp-CSDN博客
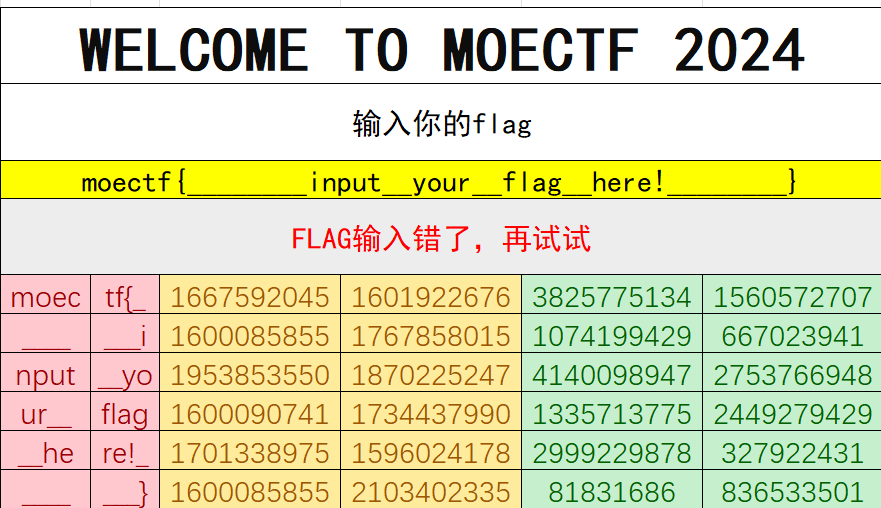
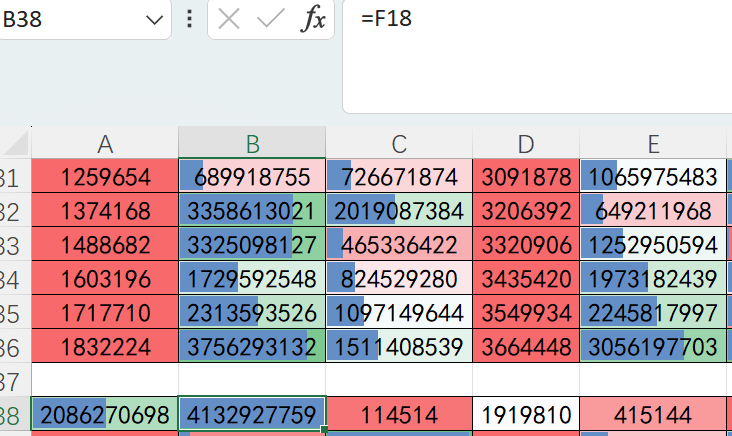
首先看到了一张表格图
从这里我们可以知道最后解密出来的密文要是这些数字
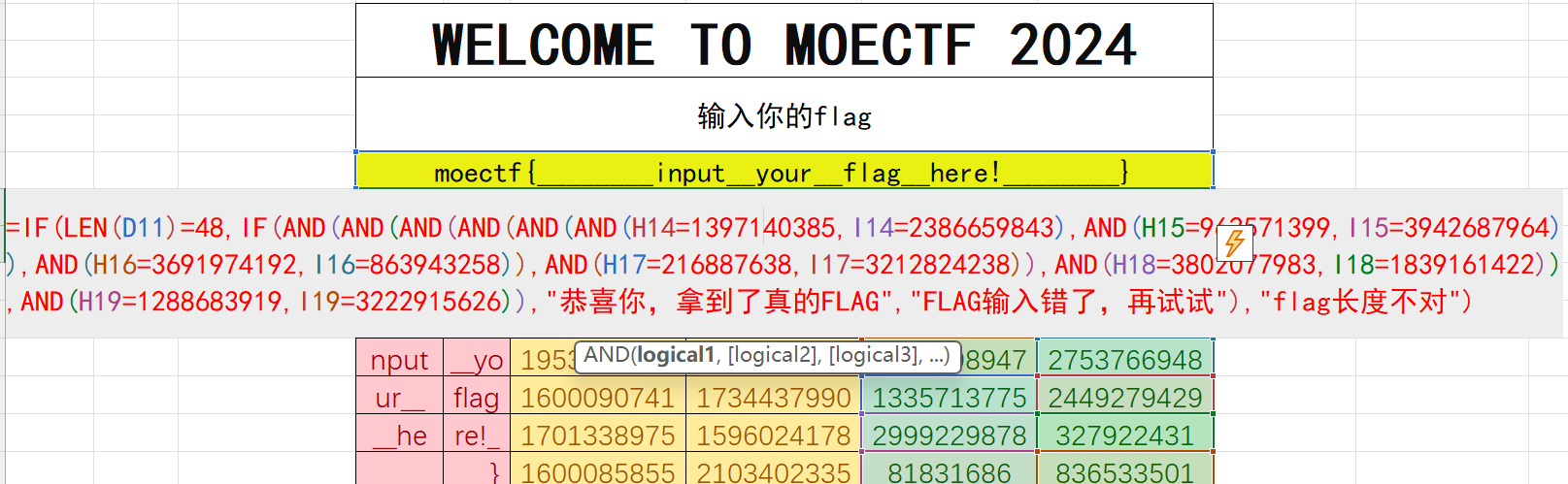
1 | 再点下面的框发现D到G都是由输入的flag所求出来的,之后后面绿的框是由s3cr3t!加密而来,而我们知道加密后的结果是上面flag的值,因此需要逆向回原文,并且每一字节转为1字符 |
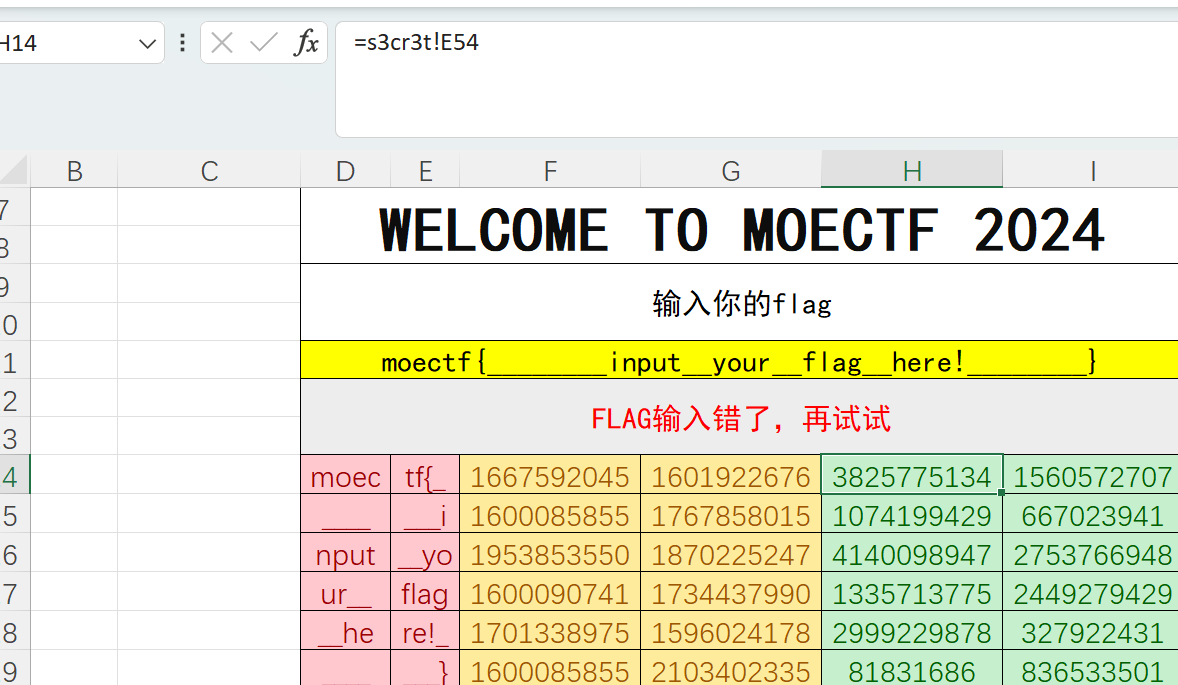
接下来看加密表格,先看上面点击的E54和F54
先来看看xlsx语法
1 | BITAND 函数返回两个数的按位进行“与”(AND)运算后的结果。 |
由此来看这句话
1
2
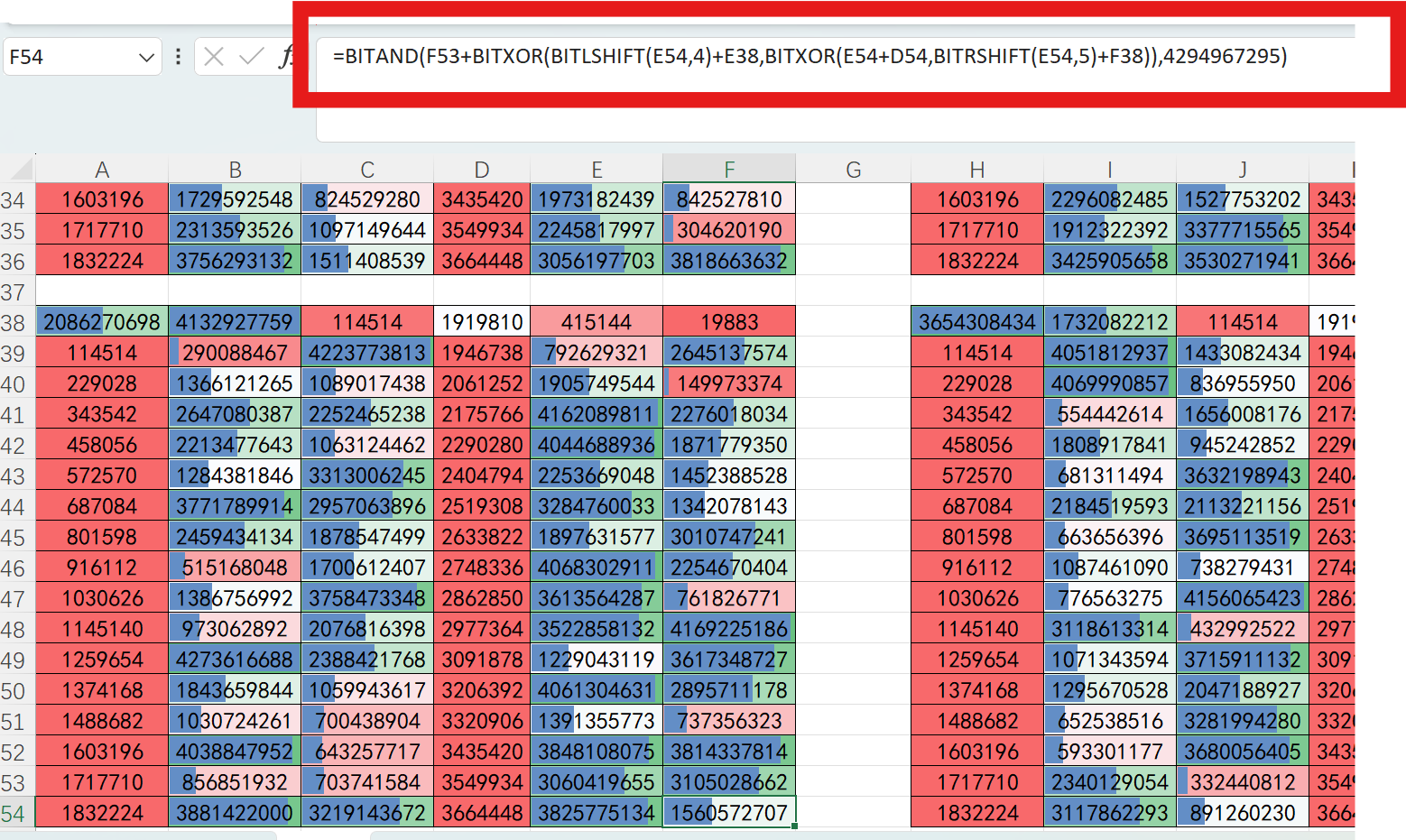
3=BITAND(F53+BITXOR(BITLSHIFT(E54,4)+E38,BITXOR(E54+D54,BITRSHIFT(E54,5)+F38)),4294967295)
翻译完就是
(F53+XOR((E54<<4))+E38,XOR(E54+D54,(E54<<5)+F38))) & 4294967295再多点几个就找到了规律:
1
2
3
4F54=(上+(左<<4+415144)^(左+3664448)^(左>>5+19883))&4294967295
B C 段用的是 114514,1919810
E F 段用的是 415144,19883
BC 和 EF 共进行32次
又由这张图发现是两次大加密,也就是总共64次,下面用上面加密的接着
至此就可以从最后的答案开始编写代码了
1 | def xor(m,n): |
SecretModule
这题是真没思路,跟着wp走一遍
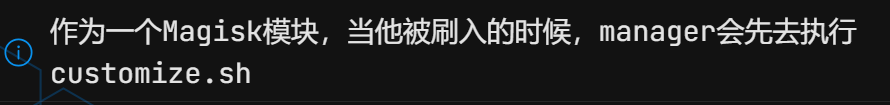
由这个我们把重点关注在customize.sh上
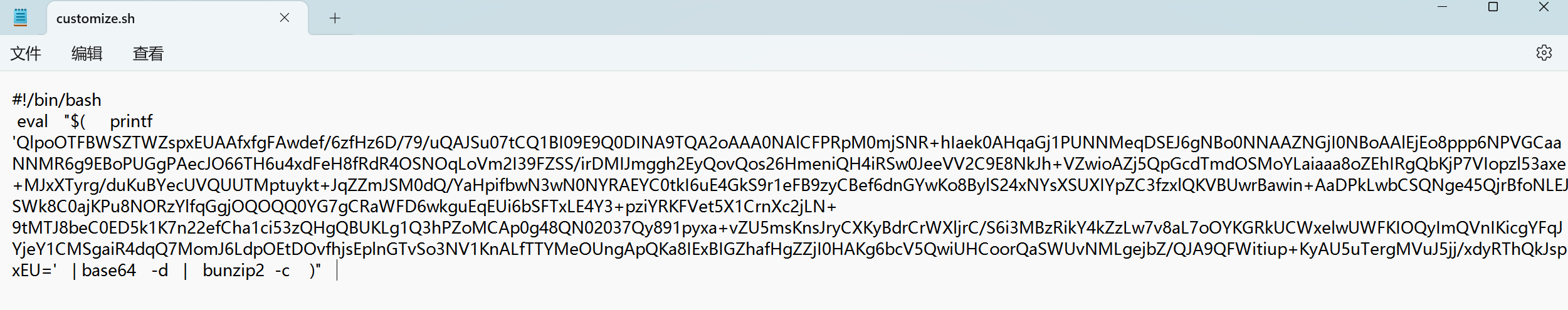
记事本打开,很明显的base64提示
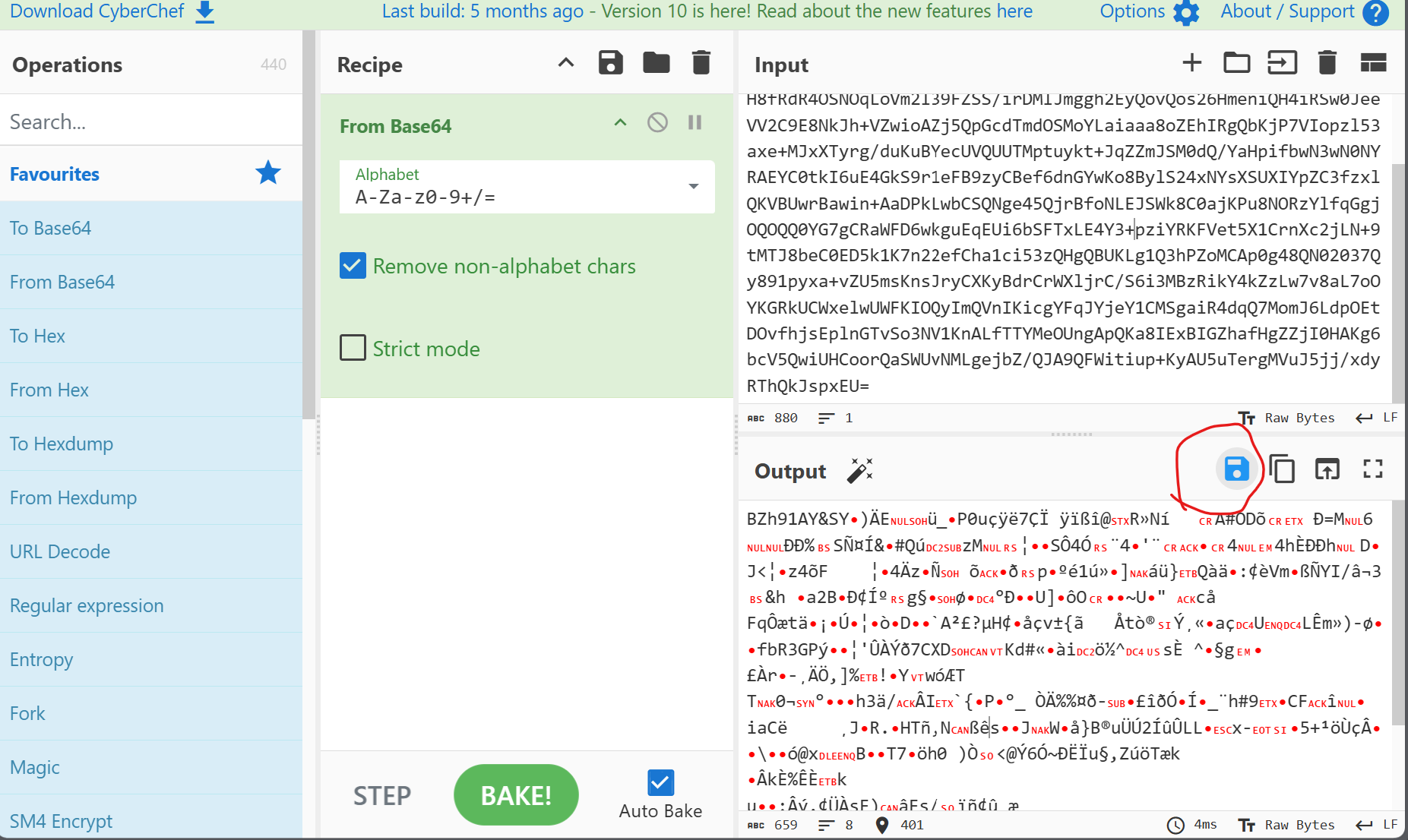
下载至本地,这里是为什么不太清楚
得到压缩包解压出来download,接着用记事本打开
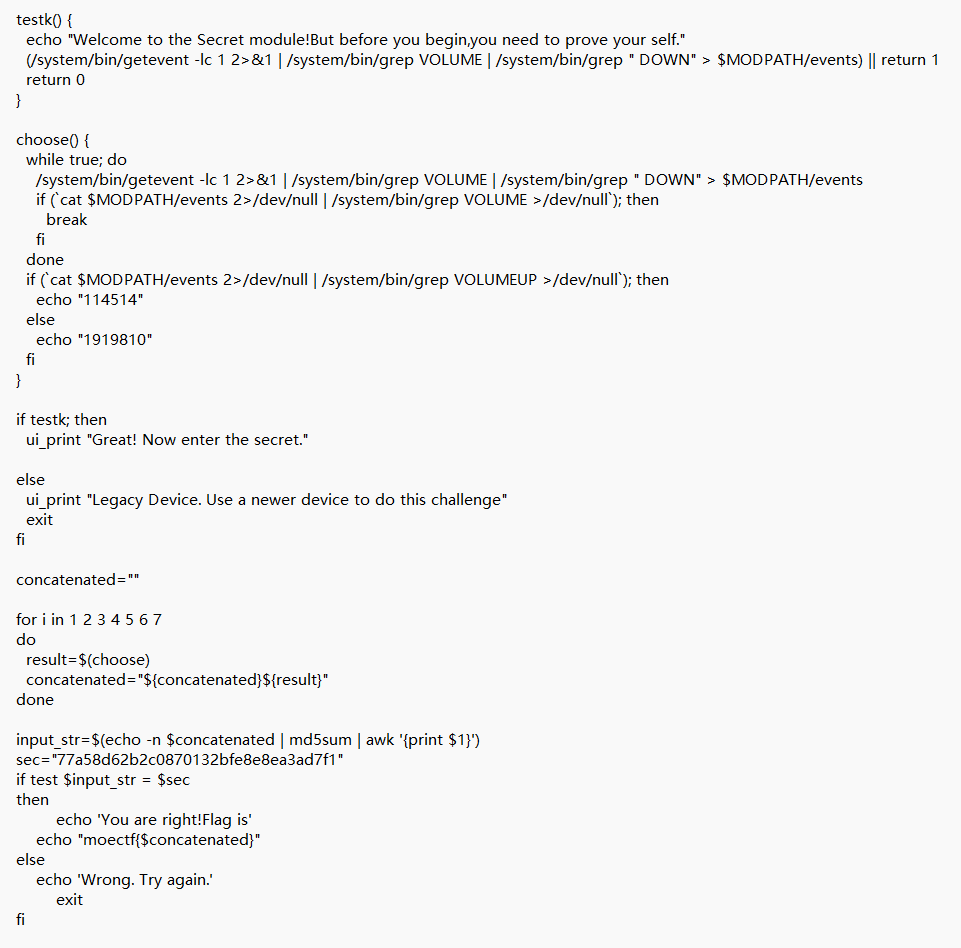
chatgpt解析一下

叫gpt秒了额

1 | import hashlib |
1 | moectf{114514114514191981011451411451419198101919810} |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来源 ᕙ(• ॒ ູ•)ᕘ欢迎光临ᕙ(`▿´)ᕗ!




